Fortify Your
Defenses with
Tailored Security
Architecture
Designing robust, scalable security solutions to protect your
organization from evolving cyber threats.
Key benefits of
Security Architecture Services.
Build a resilient infrastructure designed to withstand and mitigate cyber attacks.
Establish trust with hospitals, clinics, and patients. and create a loyal user base in a market that prioritizes privacy and safety
Secure Faster Market Entry with simplified audits, product reviews and approval cycles
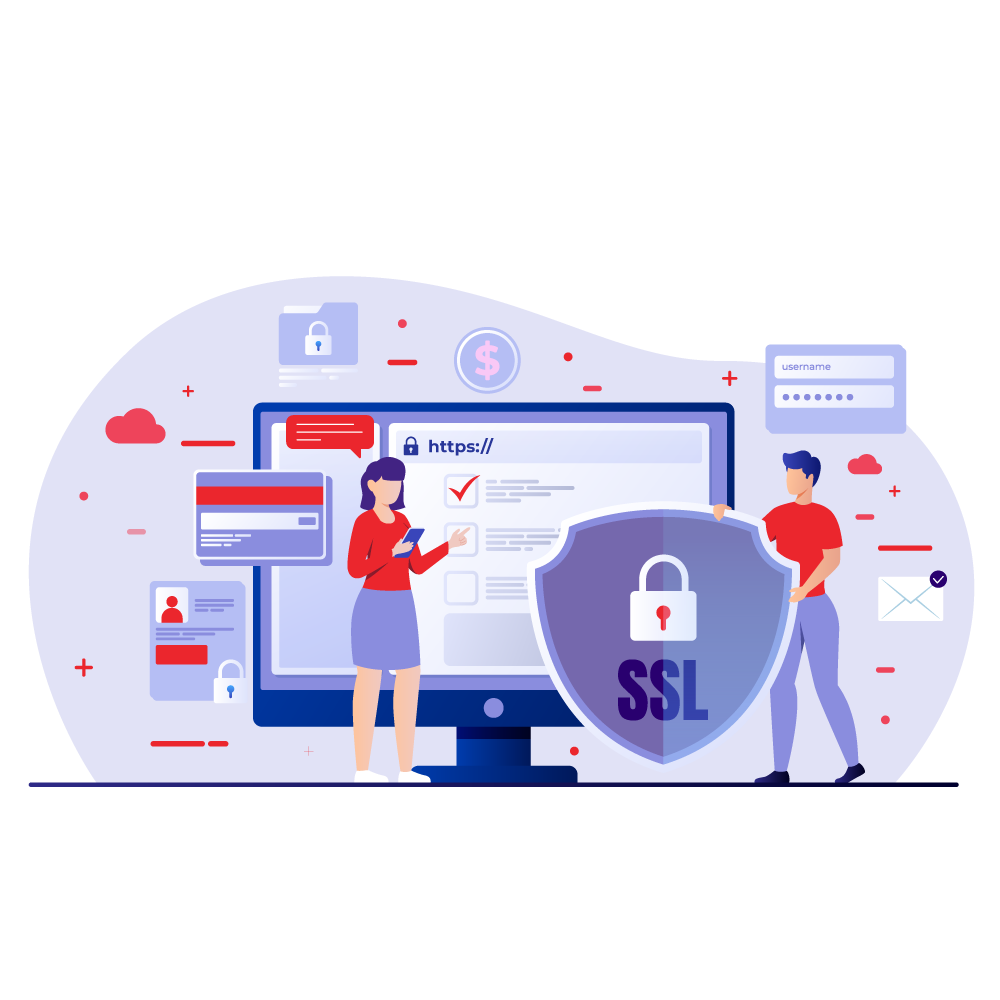
Security Architecture
We leverage proven models, methods and principles to align with your organization’s goals and design actionable security steps.
We ensure that specific security challenges are mitigated with the design recommendations intended to maintain confidentiality, integrity and availability of critical information.

Network Security
Architecture Services
This service focuses on protecting an organization’s network infrastructure from both external and internal threats by implementing strong security controls at various network layers. Our experts will assist in reviewing the customer existing N/W security infrastructure design(firewall, IPS/IDS ,VPNs, Encryption.) and provide recommendations based on their existing Security frame work /regulation /Standard followed.
Deliverables
Evaluation, Reference standards, Recommending Remediation and assist in Implementation
Purpose
To create a resilient network environment that can withstand cyberattacks, ensuring secure and reliable communication within and outside the organization.
Application
Architecture
Aiyanaar assists application teams with navigating all security patterns and processes. We verify that software tools and supporting technologies are in line with security standards and regulatory requirements. We assess the technologies, ensure their security quality is evaluated and monitored and that the security risks and findings are in line with frameworks and best practices.
Deliverables
1. Evaluation
2. Reference Standards
3. Recommending Remediation
4. Assist in Implementation


Endpoint Security
Services
These services aim to secure all endpoints—devices such as laptops, smartphones, and desktops—that connect to an organization’s network, which are often targeted by cyberattacks.
Deliverables
1. Evaluation
2. Reference Standards
3. Recommending Remediation
4. Assist in Implementation
Data Security and
Encryption Services
Focused on protecting sensitive data regardless of where it resides—whether in databases, on devices, or in transit between systems. These services ensure that data remains secure even in the event of a breach.
Deliverables
1. Evaluation
2. Reference Standards
3. Recommending Remediation
4. Assist in Implementation


Identity and Access
Management (IAM)
Services
IAM services are dedicated to managing user identities and regulating access to critical systems and data, ensuring that only authorized personnel can access sensitive information.
Deliverables
1. Evaluation
2. Reference Standards
3. Recommending Remediation
4. Assist in Implementation
When Should You
Perform Security
Architecture review?
- Before Implementing New Systems, Technologies, or Applications.
- During Major System Upgrades or Modifications.
- In Response to Emerging Threats.
- After a Security Incident or Breach.
- During Mergers, Acquisitions, or Organizational Changes.
- When There Are Changes in Compliance or Regulatory Requirements.
- When Developing or Updating Security Policies and Procedures.
- When Integrating New Business Processes or Expanding Operations.
What You Can Expect

Reduce the risk of breaches
Identify and address potential threats before they become actual security issues, reducing the risk of breaches and vulnerabilities.

Demonstrate Cyber Competency
Provide visibility of your organisation’s cyber security posture to senior management, your board, external stakeholders, regulators and clients.

Verify your Current Security Controls
Our comprehensive audits of your organisation’s infrastructure provide information about the effectiveness of your current security controls.
Tailored Security Solutions
Receive customized security recommendations and strategies that are specific to your system’s unique needs and risks.

Plan for the future
Enhance your ROI of the security programs you have in place by assessing their effectiveness through our Threat modeling service. The recommendations can be leveraged to prioritize future actions and improve your risk management programs and cybersecurity posture.
Transparent
pricing plans
Choose the Right Plan for Your Security Needs
SecComp Foundations
Custom
Enquiries
Ad-hoc – $99/hr
3rd party certifications,
FDA AINN for Cybersecurity, etc
Custom
enquiries
Ad-hoc – $99/hr
3rd party certifications,
FDA AINN for Cybersecurity, etc
View other services we offer
Tailored Solutions to Safeguard Your Digital Assets.
How can we help you out?
Reach out to us in the nearest office
Location
Austin Tx 78731
United States of
America
Location
NC 27513, USA
United States of
America
Location
Chennai 600125, Tamil nadu , india

