SecComp Foundation
What You Get
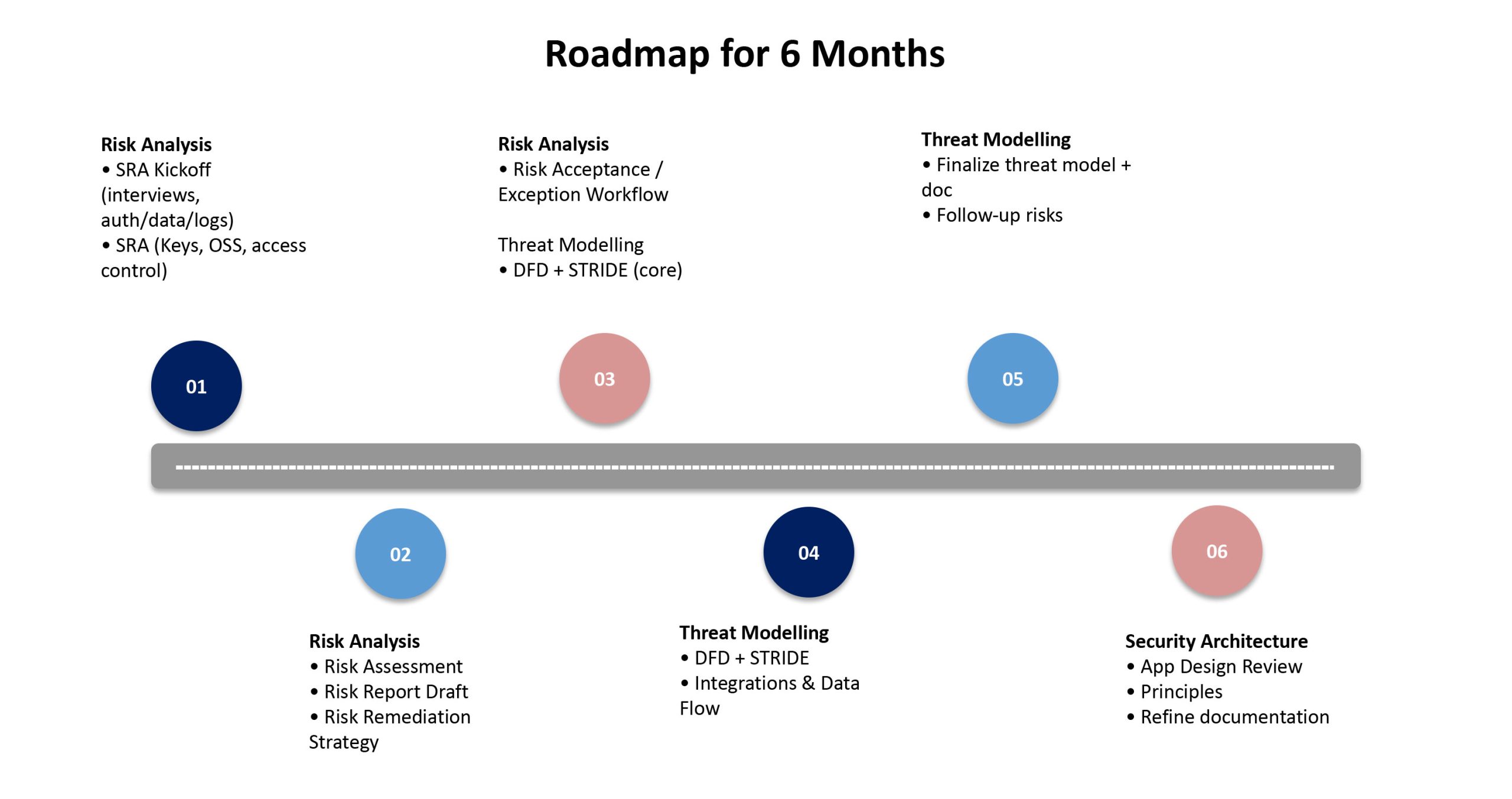
Security Risk Analysis
• Identify and prioritize security risks across your application, infrastructure, and data
• Review authentication, authorization, and access control
• Assess data protection, encryption, and key management practices
• Evaluate logging, monitoring, and incident readiness
• Create a clear risk register with remediation guidance
• Define risk acceptance and exception workflows
Threat Modelling
• Identify threat scenarios using structured methodologies (DFD, STRIDE)
• Analyse data flows, integrations, and trust boundaries
• Map threats to practical mitigations
• Produce a documented threat model that evolves with your product
Security Architecture
• Review and validate your application and cloud architecture
• Define security design principles aligned to scale and compliance
• Identify architectural gaps and improvement areas
• Deliver actionable architecture recommendations

