What You Get
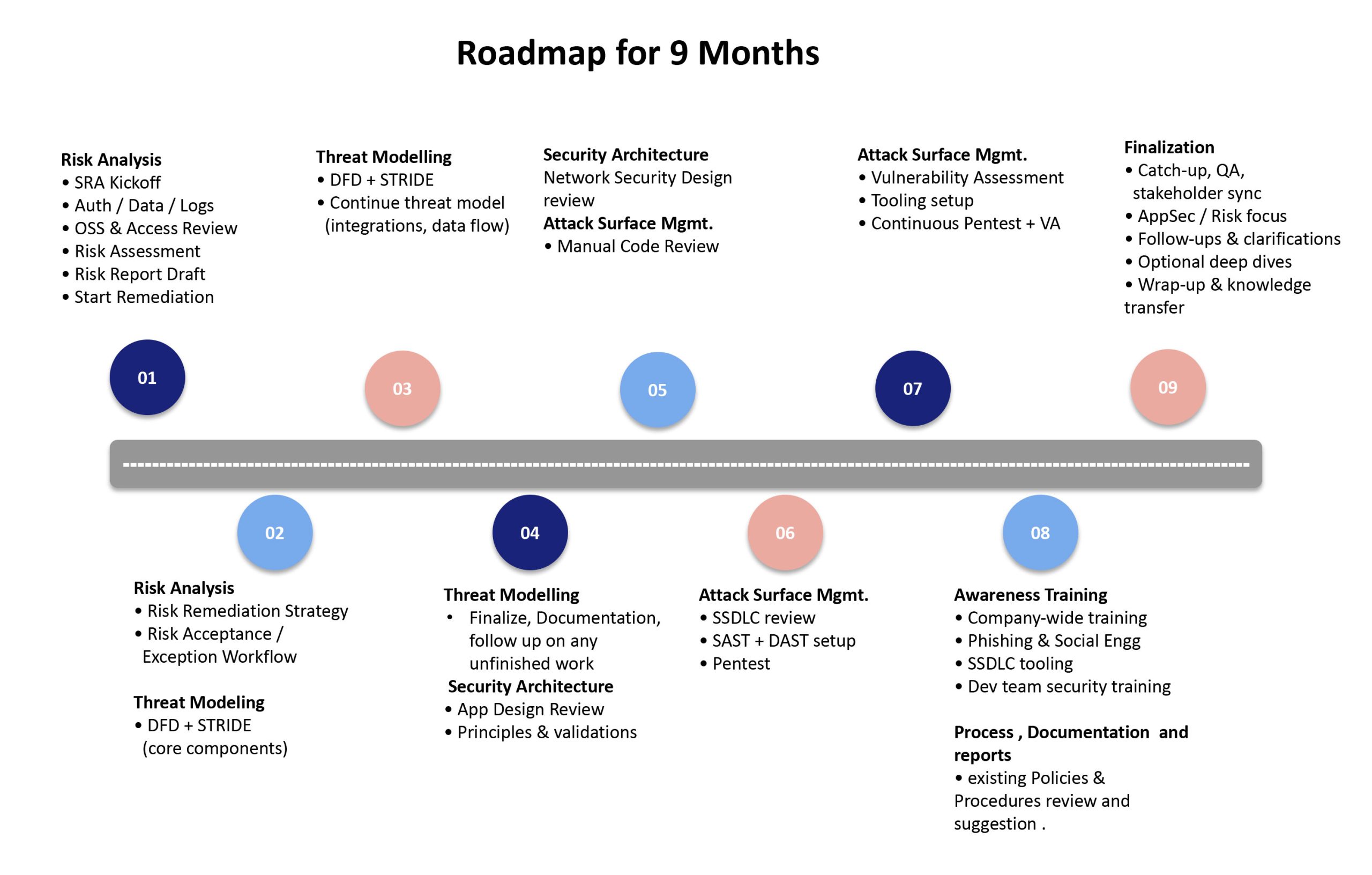
Security Risk Analysis
• Identify and prioritize security risks across your application, infrastructure, and data
• Review authentication, authorization, and access control
• Assess data protection, encryption, and key management practices
• Evaluate logging, monitoring, and incident readiness
• Create a clear risk register with remediation guidance
• Define risk acceptance and exception workflows
Threat Modeling
• Perform structured threat modeling using DFD and STRIDE methodologies
• Analyze data flows, integrations, APIs, and trust boundaries
• Identify realistic threat scenarios and attack paths
• Map threats to practical and implementable mitigations
• Maintain a documented threat model that evolves with the product
Security Architecture
• Application design review to identify architectural security gaps
• Network Security Design review
• Validate architecture against real-world threat scenarios
• Provide actionable architecture recommendations—not theoretical guidance
Attack Surface Management
• Secure code review focused on high-risk components
• Secure SDLC assessment and enablement (SAST / DAST integration)
• Penetration testing coordination and findings review
• Vulnerability assessment with remediation prioritization
Security Awareness & Training
•Cybersecurity awareness training for all employees
•Phishing and social engineering awareness programs
•Technology and tooling orientation for Secure SDLC
•Development team security training covering:
• Secure coding practices
• Common attack patterns
• Risk awareness and prevention techniques
Process , Documentation and reports
• existing Policies & Procedures review and suggestion .
Finalization
• Catch-up, QA, stakeholder sync
• AppSec / Risk focus
• Follow-ups & clarifications
• Optional deep dives
• Wrap-up & knowledge transfer