What You Get
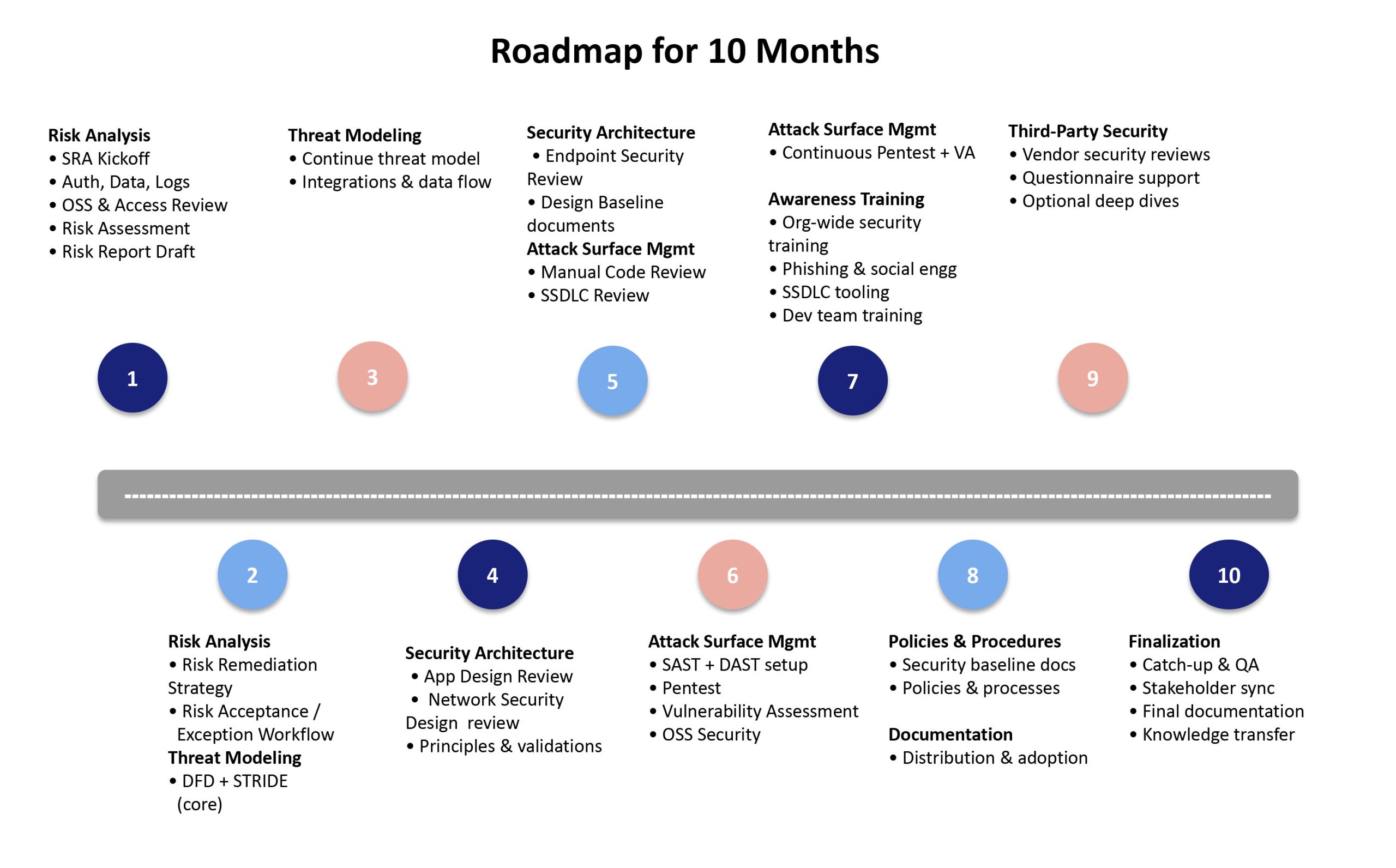
Security Risk Analysis
• Identify and prioritize security risks across your application, infrastructure, and data
• Review authentication, authorization, and access control
• Assess data protection, encryption, and key management practices
• Evaluate logging, monitoring, and incident readiness
• Create a clear risk register with remediation guidance
• Define risk acceptance and exception workflows
Threat modelling
• Perform structured threat modeling using DFD and STRIDE methodologies
• Analyze data flows, integrations, APIs, and trust boundaries
• Identify realistic threat scenarios and attack paths
• Map threats to practical and implementable mitigations
• Maintain a documented threat model that evolves with the product
Security Architecture
• Application design review to identify architectural security gaps
• Endpoint security review across servers and employee devices
• Network Security design review
• Validate architecture against real-world threat scenarios
• Provide actionable architecture recommendations—not theoretical guidance
• Design Baseline documents
Attack Surface Management
• Secure code review focused on high-risk components
• Secure SDLC assessment and enablement (SAST / DAST integration)
• Penetration testing coordination and findings review
• Vulnerability assessment with remediation prioritization
• OSS-open source software analysis
Security Awareness Training
• Cybersecurity awareness training for all employees
• Phishing and social engineering awareness programs
• Technology and tooling orientation for Secure SDLC
• Development team security training covering:
• Secure coding practices
• Common attack patterns
• Risk awareness and prevention techniques
• Compliance training for focused audience
Policies, Procedures & Documentation
• Define baseline security policies aligned to company scale
• Develop security procedures for consistent implementation
• Create documentation suitable for enterprise customers and audits
• Enable teams to follow and maintain security processes effectively
Third-Party Security
• Lightweight third-party and vendor security reviews
• Support for vendor questionnaires and security clarifications
• Optional deep-dive vendor risk assessments
• Wrap-up reporting and risk acceptance documentation
Finalization
• Catch-up & QA
• Stakeholder sync
• Final documentation
• Knowledge transfer
| Month | Category | Sub-Task(s) | Hours |
|---|---|---|---|
| 1 | Risk Analysis | SRA Kickoff (interviews, auth/data/logs) | 8 |
| Risk Analysis | SRA (keys, OSS, access control) | 8 | |
| Risk Analysis | Risk Assessment Report Draft | 6 | |
| Risk Analysis | Start Risk Remediation Strategy | 5 | |
| 2 | Risk Analysis | Start Risk Remediation Strategy | 5 |
| Risk Analysis | Risk Acceptance / Exception Workflow | 12 | |
| Threat Modelling | DFD + STRIDE (core components) | 10 | |
| 3 | Threat Modelling | DFD + STRIDE (core components), Continue threat model (integrations, data flow) | 32 |
| 4 | Threat Modelling | Finalize threat model + doc / Follow-up on any unfinished risk activities | 3 |
| Threat Modelling | Start documentation | 8 | |
| Security Architecture | App Design Review – principles and validations | 16 | |
| 5 | Security Architecture | Review outcomes + refine architecture documentation | 3 |
| Security Architecture | Start Endpoint Security Review | 6 | |
| Security Architecture | Continue Endpoint Security + Network Security Review | 10 | |
| Attack surface Management | Manual Code Review + SSDLC review | 11 | |
| 6 | Attack surface Management | SAST + DAST Tool Setup + Scanning | 12 |
| Attack surface Management | Pentest + Vulnerability Assessment | 10 | |
| Attack surface Management | Overflow from tooling setup | 3 | |
| 7 | Attack surface Management | Continue Pentest + Vulnerability Assessment | 15 |
| Awareness Training |
1. Cybersecurity training for all employees 2. Promote awareness of phishing and social engineering attacks 3. Technology for SSDLC training 4. Development Team Security Training: Train developers and teams on secure development practices and potential risks. |
6 | |
| Policies & Procedures and documentation |
Security baseline Documents will be defined for all services Security Policies and Procedures Process will be defined and will train SME’s |
5 | |
| 8 | Policies & Procedures and documentation | Refinements / Distribution | 9 |
| Finalization | Catch-up, QA, stakeholder sync, Documentation | 8 | |
| Optional Deep Dives | Security deep dives (risk or appsec focus) | 6 |